White House Warns of High-Risk Vendors in 5G Security Strategy
White house outlines 5g security strategy warns of high risk vendors – The White House has Artikeld a comprehensive 5G security strategy, warning of high-risk vendors and their potential impact on the security and reliability of 5G networks. This strategy highlights the growing concern about the vulnerability of critical infrastructure to foreign influence and emphasizes the need for robust security measures to protect sensitive data and ensure the integrity of our communication networks.
The strategy identifies specific vendors deemed high-risk due to their potential security vulnerabilities, ties to foreign governments, and concerns about data privacy. The White House aims to mitigate these risks through a combination of policy measures, technical safeguards, and collaborative efforts with industry stakeholders.
High-Risk Vendors: White House Outlines 5g Security Strategy Warns Of High Risk Vendors
The White House’s 5G security strategy highlights the significant risks posed by certain vendors, particularly those with potential ties to foreign governments or concerns about data privacy. This strategy aims to mitigate these risks and ensure the security and reliability of 5G networks in the United States.
The White House has released a 5G security strategy, highlighting the need to protect critical infrastructure from potential threats. The strategy emphasizes the importance of vetting vendors and minimizing reliance on high-risk entities. This cautious approach is reminiscent of the early days of the COVID-19 pandemic, when health officials closely monitored the recovery of early patients, providing valuable insights into the virus’s behavior.
Early US coronavirus patients have fully recovered, health officials confirmed , offering hope and data for future treatment strategies. Similarly, the 5G security strategy aims to mitigate potential risks by learning from past experiences and taking a proactive approach to safeguarding national security.
Identification of High-Risk Vendors
The White House has identified specific vendors as high-risk, citing concerns about their potential to compromise the security and integrity of 5G networks. While the document doesn’t explicitly name these vendors, it provides clear criteria for their identification.
The White House’s new 5G security strategy is a serious call to action, emphasizing the need to carefully vet vendors and protect our critical infrastructure. While the focus is on national security, it’s interesting to see how this plays out in the political landscape, with news like Biden projected to win Virginia and North Carolina, Sanders claims victory in home state Vermont dominating headlines.
This 5G security strategy is likely to be a hot topic in the coming months, especially as the US continues to grapple with the complex challenges of technological advancement and national security.
Reasons for High-Risk Designation
The White House’s concerns about high-risk vendors stem from several factors:
- Potential Security Vulnerabilities:Some vendors may have a history of security breaches or vulnerabilities in their equipment, raising concerns about their ability to protect sensitive data and infrastructure.
- Ties to Foreign Governments:Vendors with close ties to foreign governments, particularly those with adversarial relationships with the United States, may be susceptible to influence or coercion, potentially compromising network security.
- Data Privacy Concerns:Certain vendors may have questionable data privacy practices, raising concerns about the potential for misuse or unauthorized access to user data.
Impact on 5G Network Security, White house outlines 5g security strategy warns of high risk vendors
The presence of high-risk vendors in 5G networks poses significant threats:
- Data Breaches:Vulnerable equipment could lead to data breaches, compromising sensitive information such as personal data, financial records, and national security secrets.
- Network Disruptions:Malicious actors could exploit vulnerabilities to disrupt network operations, causing widespread outages and affecting critical infrastructure.
- Espionage and Surveillance:Foreign governments could use compromised equipment to conduct espionage and surveillance activities, potentially targeting individuals, businesses, and government agencies.
Mitigation Strategies and Recommendations
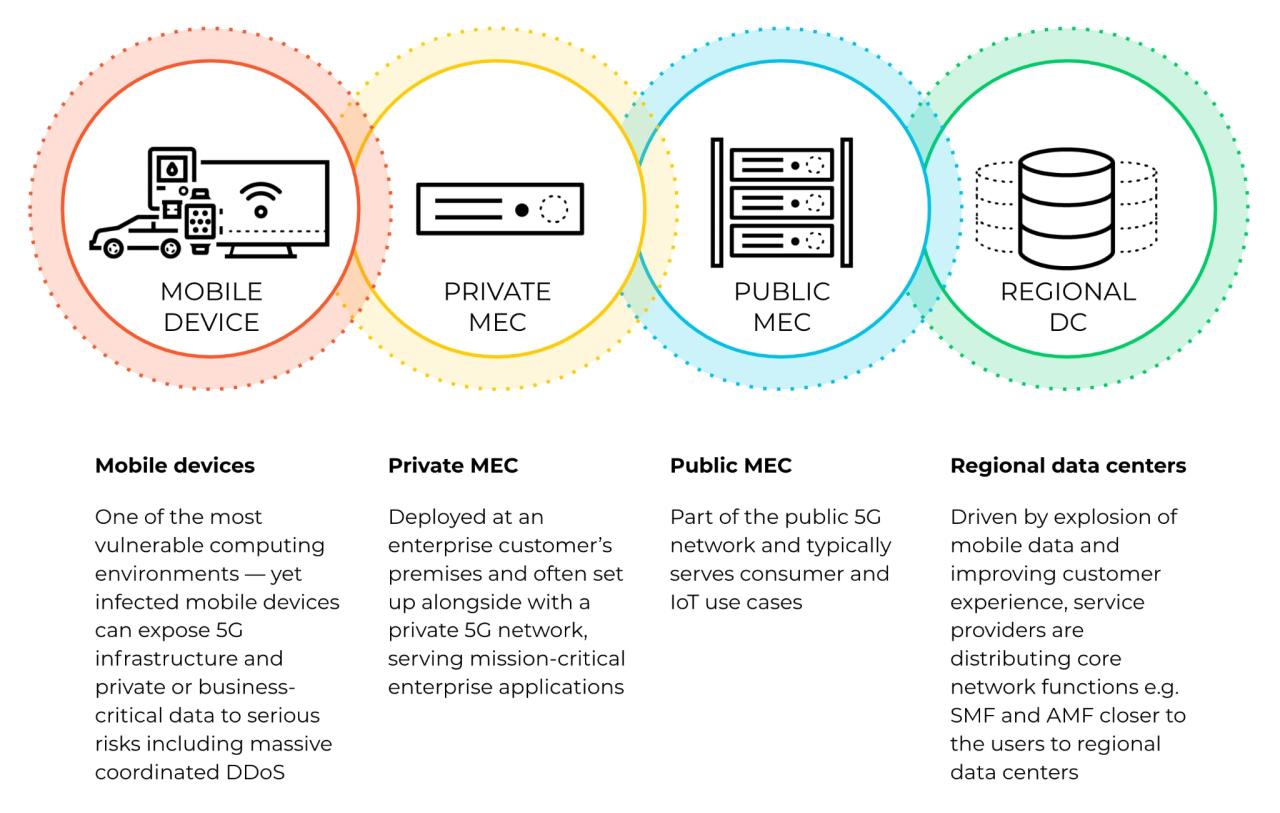
The White House’s 5G security strategy Artikels a comprehensive approach to mitigating the risks posed by high-risk vendors. This strategy focuses on a multi-pronged approach, combining regulatory measures, technological advancements, and collaborative efforts to ensure the secure deployment of 5G networks.
Strategies for Mitigating Security Risks
The White House’s mitigation strategies aim to address the vulnerabilities associated with high-risk vendors by minimizing their influence on critical 5G infrastructure. These strategies are designed to enhance network security, protect sensitive data, and maintain the integrity of communications.
- Restricting Access to Critical Infrastructure:The strategy emphasizes limiting the involvement of high-risk vendors in the core network, which handles sensitive data and network traffic. This restriction aims to prevent potential backdoors and unauthorized access to critical infrastructure.
- Promoting Diversification of Suppliers:The White House encourages the use of multiple vendors for 5G network components, reducing reliance on any single supplier and creating a more resilient network. This diversification helps to mitigate the impact of potential vulnerabilities in a single vendor’s equipment.
- Investing in Secure Technologies:The strategy calls for investments in advanced security technologies, including encryption, intrusion detection systems, and threat intelligence platforms. These technologies are designed to detect and prevent malicious activity, enhancing the overall security posture of 5G networks.
- Enhancing International Cooperation:The White House recognizes the importance of international collaboration to address the global nature of 5G security risks. This strategy encourages working with allies to share best practices, coordinate security measures, and develop common standards for secure 5G deployment.
Recommendations for Individuals, Businesses, and Government Agencies
The White House’s 5G security strategy provides recommendations for various stakeholders to strengthen their security posture and contribute to a secure 5G ecosystem.
The White House’s new 5G security strategy is raising eyebrows, particularly with its warnings about high-risk vendors. The strategy, aimed at securing America’s 5G network, highlights the potential vulnerabilities of relying on untrusted companies, especially those with ties to foreign governments.
This focus on security comes at a time when the US is grappling with a global pandemic, and the news cycle is dominated by stories like Trump’s fury over Americans infected with coronavirus returning to the US without his permission.
While the two issues seem unrelated, they both underscore the importance of prioritizing national security and safeguarding against potential threats, whether they come from foreign actors or a global health crisis.
Individuals
- Use Strong Passwords and Multi-Factor Authentication:Individuals should prioritize strong passwords and enable multi-factor authentication for their online accounts, including those related to mobile devices and 5G services. This helps to protect against unauthorized access and data breaches.
- Be Cautious of Phishing Attempts:Individuals should be vigilant about phishing emails, text messages, and other forms of social engineering attacks. These attacks often try to trick users into providing sensitive information or downloading malicious software.
- Keep Devices and Software Updated:Regularly updating operating systems, apps, and security software patches vulnerabilities and helps to protect against known threats.
Businesses
- Conduct Thorough Due Diligence on Vendors:Businesses should carefully evaluate the security practices and track records of potential 5G vendors. This due diligence process should include assessing the vendor’s security controls, compliance with industry standards, and past incidents.
- Implement Strong Access Controls:Businesses should establish robust access controls for their 5G networks, limiting access to authorized personnel and ensuring proper authentication and authorization mechanisms.
- Develop a Comprehensive Security Policy:Businesses should create a comprehensive security policy that Artikels their approach to 5G security, including data protection, incident response, and security awareness training for employees.
Government Agencies
- Promote Secure 5G Deployment:Government agencies should play a leading role in promoting secure 5G deployment by establishing clear guidelines, standards, and best practices for the industry.
- Invest in Research and Development:Government agencies should invest in research and development of advanced security technologies and solutions to address emerging threats in the 5G ecosystem.
- Foster Collaboration and Information Sharing:Government agencies should encourage collaboration and information sharing between industry stakeholders, researchers, and law enforcement agencies to enhance situational awareness and facilitate timely responses to security incidents.
Impact on 5G Deployment and Industry
The White House’s 5G security strategy, focused on mitigating risks associated with high-risk vendors, is likely to have significant implications for the deployment of 5G networks in the United States and the telecommunications industry as a whole. This strategy, emphasizing security and trust, could influence the pace and direction of 5G development, while also impacting the economic and technological landscape.
Impact on 5G Deployment
The White House’s strategy, by promoting the use of trusted vendors and discouraging reliance on those deemed high-risk, could potentially slow down the deployment of 5G networks in the United States. This is because:
- Vendor Restrictions:The strategy may limit the pool of available vendors, particularly for critical network components, leading to longer procurement processes and potential delays in network construction.
- Increased Costs:Choosing vendors based on security considerations could increase the cost of 5G network deployment, as trusted vendors might charge higher prices or require more stringent security measures.
- Technical Challenges:Implementing security measures can be technically complex and require significant expertise, potentially leading to delays in network deployment.
Impact on Telecommunications Industry
The strategy’s impact on the telecommunications industry is multifaceted, potentially leading to:
- Realignment of Supply Chains:The industry may need to adapt its supply chains to incorporate trusted vendors, potentially leading to new partnerships and disruptions in existing relationships.
- Technological Innovation:The emphasis on security could stimulate innovation in the development of secure 5G technologies, leading to advancements in encryption, authentication, and other security measures.
- Economic Implications:The strategy could have both positive and negative economic consequences. While it may lead to increased investment in domestic security solutions, it could also impact the competitiveness of US telecommunications companies in the global market.
Comparison with Other Countries
The United States’ 5G security approach differs from those adopted by other countries. For instance:
- China:China has heavily invested in its own 5G technology and infrastructure, prioritizing domestic vendors and promoting a closed ecosystem. This approach prioritizes national control but may limit interoperability with other countries.
- European Union:The EU has adopted a more collaborative approach, promoting open standards and encouraging cooperation between countries. While prioritizing security, the EU aims to maintain a balance between security and innovation.
Epilogue

The White House’s 5G security strategy underscores the importance of a multi-faceted approach to safeguarding our critical infrastructure in the face of evolving threats. The strategy emphasizes the need for vigilance, collaboration, and continuous adaptation to ensure the security and reliability of our 5G networks.
As the world becomes increasingly reliant on 5G technology, the need for robust security measures will only grow more critical.